SHELL CONTROL BOX
Shell Control Box is a user monitoring appliance that controls privileged access to remote IT systems, records activities in searchable, movie-like audit trails, and prevents malicious actions. SCB is a quickly deployable enterprise device, completely independent from clients and servers – integrating seamlessly into existing networks. SCB is a core component of the Contextual Security Intelligence Suite. It captures the activity data necessary for user profiling and enables full user session drill down for forensic investigation in CSI.User.
CENTRAL POLICY ENFORCEMENT
SCB acts as a centralized authentication and access-control point in your IT environment which improves security and reduces user administration costs. The granular access management helps you to control who can access what and when on your servers.
ADVANCED PROTECTION OF SENSITIVE DATA
SCB perfectly isolates your sensitive systems from unknown intruders or from non-authorized users. In addition, it tracks all authorized access to sensitive data and provides with actionable information in the case of human errors or unusual behavior.
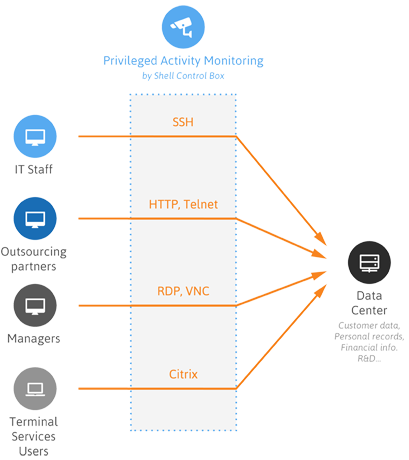
PREVENTION OF MALICIOUS ACTIVITIES
SCB monitors privileged user sessions in real-time and detects anomalies as they occur. In case of detecting a suspicious user activity (for example entering a destuctive command, such as the “delete”), SCB can send you an alert or immediately terminate the connection.
TIGHTER EMPLOYEE & PARTNER CONTROL
SCB audits “who did what”, for example on your database or SAP servers. Aware of this, your employees will do their work with a greater sense of responsibility leading to a reduction in human errors. By having an easily interpreted, tamper-proof record, finger-pointing issues can be eliminated.
FASTER, COST-EFFECTIVE SUPERVISORY AUDITS
SCB makes all user activity traceable by recording them in high quality, tamper-proof and easily searchable audit trails. The movie-like audit trails ensure that all the necessary information is accessible for ad-hoc analyses or custom activity reports.
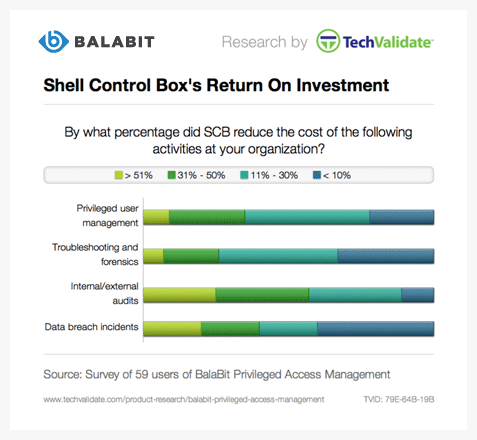
LOWER TROUBLESHOOTING & FORENSICS COSTS
When something wrong happens, everybody wants to know the real story. Analyzing thousands of text-based logs can be a nightmare and may require the participation of external experts. The ability to easily reconstruct user sessions allows you to shorten investigation time and avoid unexpected cost.
PRODUCT FEATURES AND BENEFITS
GRANULAR ACCESS CONTROL
SCB acts as an application level proxy gateway. The transferred connections and traffic are inspected on the application level (Layer 7 in the OSI model), rejecting all traffic violating the protocol – an effective shield against attacks. This high-level understanding of the traffic gives control over the various features of the protocols, like authentication and encryption methods used in SSH connections, or channels permitted in RDP traffic.
- Support for SSH, RDP, HTTP(s), Citrix ICA, Telnet, TN3270/TN5250, VNC, X11 and VMware View protocols
- Control protocol specific channels, such as terminal sessions, disk-mapping or file sharing
- Audit SCP, SFTP and HTTP(s) based file transfers
- Detailed access control based on time and user group policies
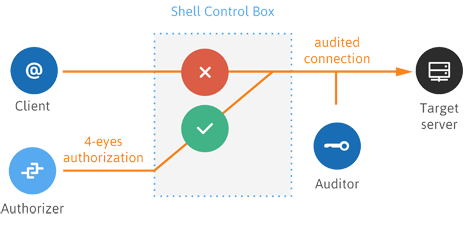
STRONG AUTHENTICATION AND AUTHORIZATION
SCB can enforce the use of two-factor authentication methods and also verify the public key of the users. SCB has a built-in capability to verify the SSH host keys and certificates identifying the servers, preventing man-in-the-middle attacks and other threats. This authentication is completely independent from the authentication that the user performs on the remote server. To avoid accidental misconfiguration and other human errors, SCB supports the 4-eyes authorization principle as well.
- Gateway authentication
- Integration with authentication databases (for example, Microsoft AD, LDAP or RADIUS) and multifactor authentication backends
- User-mapping policies – describe who can use a shared user (e.g. “root”) to access the remote server
- Password vaulting – use the built-in Credential Store, or integrate with a third-party password management system
- Server-side auto-login with SCB impersonating the authenticated user on the server
- “4 eyes” authorization – the authorizer can allow, track, and even terminate the administrator’s access to the server
HIGH QUALITY AUDIT & FORENSICS
SCB operates transparently and extracts information directly from the communication of the client and the server, providing reliable, easy-to-access metadata and content. SCB records all sessions into searchable audit trails, making it easy to find relevant information in forensics or troubleshooting situations. Audit trails can be browsed online, or followed real-time to monitor the activities of the privileged users. The web-based Audit Player application replays the recorded sessions just like a movie – all actions of the administrators can be seen exactly as they appeared on their monitors. The Audit Player enables fast forwarding during replays, searching for events (for example, mouse clicks, pressing Enter) and text seen by the user.
- Complete documentation about ALL remote system accesses
- Tamper-proof (encrypted, signed and time-stamped) audit trails
- Movie-like playback of recorded sessions
- Fast, free-text search in sessions
- Custom activity and compliance reports
REAL-TIME ALERTING AND BLOCKING
SCB can monitor traffic in real time, and execute various actions if a certain, predefined pattern appears in the command line or on the screen. In the case of detecting a suspicious user action (e.g. a destructive command or an unwanted windows application), SCB can perform the following measures:
- Send an e-mail or SNMP alerts about the event
- Immediately terminate the connection
- Log the event in the system logs
- Store the event in the connection database of SCB
EASY-TO-USE GUI
SCB is configured from a clean, intuitive web interface. The roles of each SCB administrator can be clearly defined using a set of privileges – management of SCB as a host, management of connections to servers, viewing audit trails and reports, and so on.
- Granular access control to SCB GUI
- User-friendly, web-based search interface