‘You are breached’ is a phrase that no security or business executive wants to hear. Cyberattacks targeting critical infrastructure and data are an issue facing every industry, and any critical systems and applications that aren’t protected by phishing-resistant multi-factor authentication (MFA) creates a security threat gap.
Closing the gap requires the highest levels of security where most threats emerge—at the human layer. Look no further, the phishing-resistant YubiKey protects your people, data, and technology against phishing attacks and account takeovers. With these key best practices accelerate your organization’s deployment of phishing-resistant MFA at scale to keep the bad actors out.
Deployment best practices to enhance security with phishing-resistant MFA
 Security is only as strong as your weakest link
Security is only as strong as your weakest link
Depending on how diligently your users put authentication workflows into daily practice indicates how secure you really are. While identifying an effective authentication solution is the right first step, putting deployment best practices into place that accelerate and encourage user adoption is critical to enhancing the security posture of an organization.
Best practices to accelerate your YubiKey deployment
To protect against modern cyberthreats, Yubico offers the YubiKey, a hardware security key for phishing-resistant two-factor (2FA), multi-factor (MFA), and passwordless authentication at scale. Organizations worldwide are deploying YubiKeys to ensure secure user access to business networks, data, applications, and to reduce operating costs. YubiKeys help organizations across industries and the government secure their employees, customers, and supply chains against cyberthreats, enabling them to drive regulatory compliance.
Yubico’s Professional Services team can provide technical and operational guidance to help streamline your YubiKey implementation and rollout with services mapped to your needs.
Below are some of the key best practices we recommend to help you accelerate your organization’s deployment of phishing-resistant MFA.
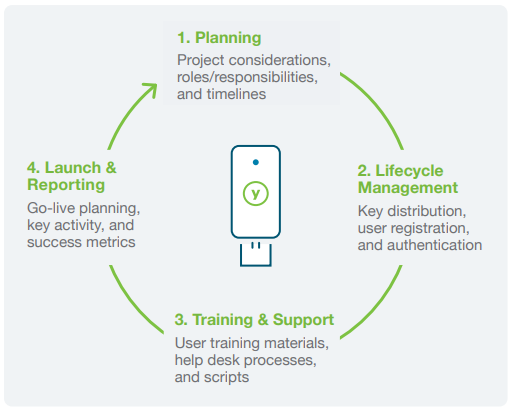
- Planning: Covering all angles
As a first step, it’s best to develop a phased approach to ensure a frictionless deployment of YubiKeys. A holistic plan that clearly identifies all users and use cases for phishing resistant MFA across your entire organization and supply chain is a must. A successful deployment also involves a variety of roles and responsibilities such as technical implementation tasks, lifecycle management, and operational components such as training, support, launch and reporting. Examples of key process questions include:
- What are your users’ needs, behaviors and risk profiles?
- Have you included all appropriate departments in planning meetings for your YubiKey deployment journey?
- Do you have cross-functional alignment?
- Lifecycle Management: Empowering users with YubiKeys
Yubico makes it very convenient to get phishing-resistant MFA directly into the hands of your employees and supply chain vendors to increase security and improve productivity. Through services such as YubiEnterprise Subscription which provides a service-based and affordable model for purchasing YubiKeys, and YubiEnterprise Delivery which provides a turnkey distribution service, Yubico can help you get YubiKeys to anywhere you need them. Key questions to ask as you prepare to distribute and manage your YubiKeys:
- Where are most of your users located—in-office, remote or hybrid?
- How will users, especially remote users, receive the YubiKey?
- How will you manage lost keys?
Once your users have their YubiKeys, the next step involves registering the keys with the applications and devices they will use. We recommend that each user has a second YubiKey as a backup, and if users cannot locate a YubiKey, revoking and replacing keys is the recommended next step. If a user leaves the organization, some organizations retrieve YubiKeys prior to their departure while others prefer to allow departing users to keep their YubiKeys and continue using it for their own personal accounts.
- Training & Support: Spreading awareness
The next important step is effective education and awareness, in order to showcase to your user community why the company invested in the YubiKey, and the direct benefits to users. The YubiKey’s simple user experience requires minimal training and on-going support for users. However, should users require additional guidance, there are a variety of training approaches, including in-person and virtual webinars, and how-to videos that can be utilized. Key questions to ask:
- How will you train and support users?
- Do you have a communication plan with accessible assets that will help support users?
- Reporting & Launch: Evaluate for lift-off
After a comprehensive plan is created, it’s also important to map out the various metrics that will be beneficial to capture to show success, such as:
- Number of keys distributed
- Number of users activated
- Applications enabled
- Security threats mitigated
- Reduction in password reset-related IT support calls
- Productivity related to user log-in times
Having clear visibility through reports, or even by conducting user surveys can provide extra clarity back to the business. Key questions to ask:
- How will you measure the progress and success of your deployment?
- What specific metrics make sense for your organization?

Yubico is ready to help
The Yubico Professional Services team is composed of knowledgeable security professionals with experience gained from hundreds of customer implementations across a wide range of industries. From standard implementations to complex enterprise rollouts, Yubico Professional Services has the skills and expertise to help guide you through all technical and operational facets of a YubiKey implementation and deployment. You can embrace the YubiKey with confidence, knowing that you have a solution and the right experts in place to prevent account takeovers and empower your users. Get started today!
About DT Asia
DT Asia began in 2007 with a clear mission to build market entry for various pioneering IT security solutions from US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around Asia Pacific to better understand the markets and deliver localised solutions.
Learn more: https://dtasiagroup.com/yubico/


