Protect & Secure
Information security is designed to protect the confidentiality, integrity and availability of computer systems and physical data from unauthorised access whether with malicious intent or not. Confidentiality, integrity and availability are referred to as the CIA triad.
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.

SecureData — Hardware-Encrypted Storage & Secure Data Protection
SecureData specialises in hardware-encrypted storage solutions designed to protect sensitive data at rest and in transit. The company delivers FIPS-validated, tamper-resistant encrypted drives for enterprises, government agencies, and regulated industries requiring strict data protection and compliance.
SecureData products ensure data remains protected even if devices are lost, stolen, or physically compromised.
Key Highlights
- Protects data at rest and in transit
- Hardware-based AES-256 encryption (no software dependency)
- FIPS 140-2 / 140-3 validated security architecture
- PIN-authenticated access directly on the device
- Tamper-resistant & self-destruct protection
- Designed for government, defence, finance, healthcare & enterprise use

Featured products:
SecureDrive® BT
SecureDrive® KP
SecureUSB® BT
SecureUSB® KP
SecureDrive® Duo
SecureUSB® Duo
Remote Management (RM)



Rimini Street — Enterprise Software Support & Managed Services
Rimini Street provides premium third-party support and managed services for enterprise applications such as SAP, Oracle, VMware, Salesforce, and mission-critical databases. Their services help organisations reduce maintenance costs, extend the lifespan of existing systems, and avoid forced upgrades — while ensuring high-quality support and operational continuity.
With guaranteed long-term support, 24/7 global engineers, and dedicated Primary Support Engineers (PSE), Rimini Street delivers a high-assurance alternative to vendor support for organisations seeking stability, cost optimisation, and innovation freedom.
Why Choose Rimini Street?
- Guaranteed long-term support for SAP ECC and S/4HANA (up to 2040)
- Significant cost reduction compared to vendor maintenance fees
- 24/7/365 global support with fast SLAs and dedicated PSE
- Support for customisations and complex enterprise environments
- Regulatory, tax, and compliance updates included
- Application, database, and infrastructure expertise across SAP, Oracle, VMware and more
- No forced upgrades — allowing customers to modernise on their own roadmap
- Unified support and managed services across applications and technology stacks
Rimini Support™
Key Highlights:
- Comprehensive third-party software support for SAP, Oracle, Salesforce, VMware, and other enterprise platforms
- Covers bug fixes, break/fix, performance, interoperability and configuration
- Support for custom code/customised systems
- 24/7/365 global support with guaranteed SLA
- Helps eliminate mandatory vendor upgrades
Rimini Manage™
Key Highlights:
- Managed services for SAP, Oracle, database platforms, and enterprise applications
- Unlimited tickets and proactive issue resolution
- Includes system administration, operational support, and health monitoring
- Ideal for organisations reducing operational load on internal IT teams
Rimini Consult™
Key Highlights:
- Advisory, implementation, integration, and optimisation services
- Supports migration planning, customisation, configuration, and project-based work
- Helps organisations evolve existing systems without disruptive upgrades
Rimini Connect™
Key Highlights:
- Interoperability services that ensure enterprise apps continue working with modern OS, browsers, email systems, and infrastructure
- Avoids unnecessary application upgrades
- Extends the life of legacy systems while maintaining compatibility
Rimini Protect™
Key Highlights:
- Application and database security services
- Continuous protection against vulnerabilities and emerging threats
- Reduces risk without requiring intrusive system changes or mass upgrades
Rimini Watch™
Key Highlights:
- 24/7 monitoring for application and database health
- Detects anomalies, performance degradation, and system risks early
- Helps prevent outages and ensures system stability

Featured products:
Rimini Support™
Rimini Manage™
Rimini Consult™
Rimini Connect™
Rimini Protect™
Rimini Watch™

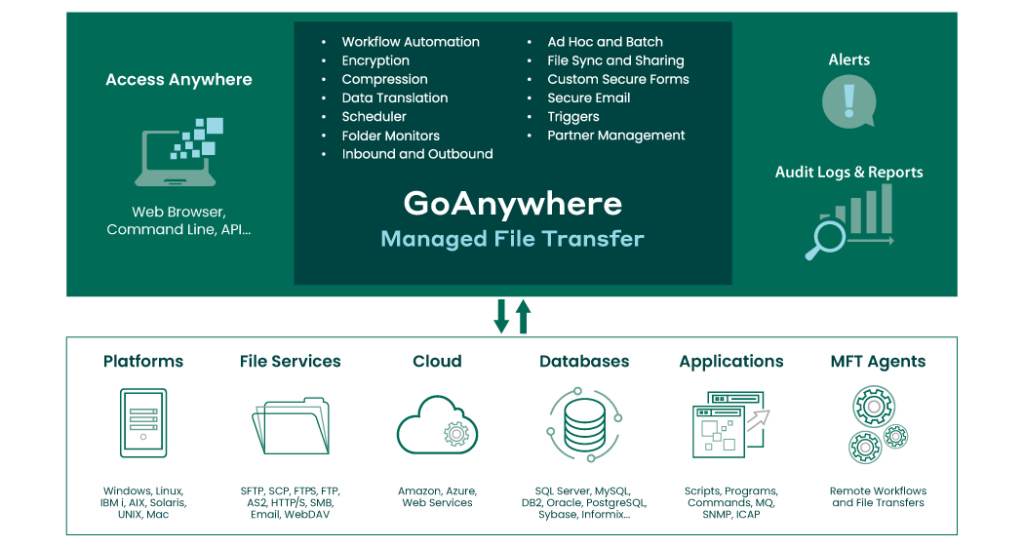
Automate & secure file transfers to protect sensitive data
GoAnywhere MFT, by Fortra, is an enterprise-grade secure managed file transfer platform designed to protect sensitive data exchanged between internal systems, business partners, and cloud environments. The solution centralises, automates, encrypts, and audits file transfers to ensure security, compliance, and operational efficiency across the organisation.
Key Highlights
- Trusted by enterprises for secure data exchange at scale
- Centralised control for all file transfer activities
- End-to-end encryption (in transit and at rest)
- Automated workflows to replace manual file transfer processes
- Comprehensive auditing & reporting for compliance
- Supports on-prem, cloud, and hybrid environments
GoAnywhere Managed File Transfer (MFT)
Key Features:
- Secure File Transfer Protocols
Supports SFTP, FTPS, HTTPS, AS2, AS4 and other secure protocols. - Encryption & Data Protection
Strong encryption for data in transit and at rest, ensuring confidentiality and integrity. - Automation & Workflow Orchestration
Automates file transfers, data processing, and system-to-system integrations without scripts. - Secure Web Client & Secure Mail
Enables users to securely send and receive files via browser-based access. - Centralised Management Dashboard
Single interface to manage users, workflows, keys, certificates, and transfer activity. - Audit Trails & Compliance Reporting
Detailed logging and reporting to support regulatory requirements (GDPR, HIPAA, PCI DSS, etc.). - High Availability & Scalability
Built to support enterprise-scale deployments with clustering and failover.

Featured products:
GoAnywhere Managed File Transfer (MFT)
A1Data — Advanced Data Recovery & Forensics Engineering
A1Data is a highly specialized data recovery provider with over 30 years of experience and more than 80,000 successful cases, equipped to handle the most complex physical and logical data loss scenarios. With 13 fully equipped clean benches (4 Class 100 and 9 Class 1000), dedicated imaging stations, and an inventory of over 30,000 donor media and spare parts, A1Data delivers industry-leading recovery results across all major storage manufacturers and device types.
Trusted by enterprises and technical teams across the region, A1Data applies strict forensic handling, advanced imaging workflows, and deep RAID reconstruction expertise to ensure maximum recoverability while minimizing processing time and risk.
Why Choose A1Data?
- 30+ years of technical expertise & 80,000+ successful recoveries
- High-capacity cleanroom facilities with 13 clean benches (Class 100 & Class 1000)
- 30,000+ donor drives & spare components available for rapid part replacement
- Forensic-grade imaging workflow ensuring no write operations to original media
- Improved recovery rate & faster turnaround through repeated analysis on cloned image data
- Specialized RAID reconstruction experts capable of fixing corrupted array structures
- Suitable for: enterprises, government, critical operations, forensic investigations
1. Enterprise Data Recovery (HDD, SSD, Flash, Server Storage)
- Recovery of severely physically damaged media (head crash, platter damage, controller failure)
- Cleanroom-based component replacement using donor parts
- Imaging-based workflow ensuring secure, repeatable investigation
2. RAID Recovery & Reconstruction
- Repair of corrupted RAID metadata
- Recovery from multi-drive failures and partial rebuilds
- Reconstruction of RAID 0, 1, 5, 6, 10 and hybrid enterprise arrays
3. Forensic & Secure Handling
- Strict “no write” methodology to original media
- Controlled cleanroom environment with particle monitoring
- Multiple imaging stations for parallel case processing

Featured product:
Enterprise Data Recovery (HDD, SSD, Flash, Server Storage)
RAID Recovery & Reconstruction
Forensic & Secure Handling

Protect & Secure