Protect and Secure
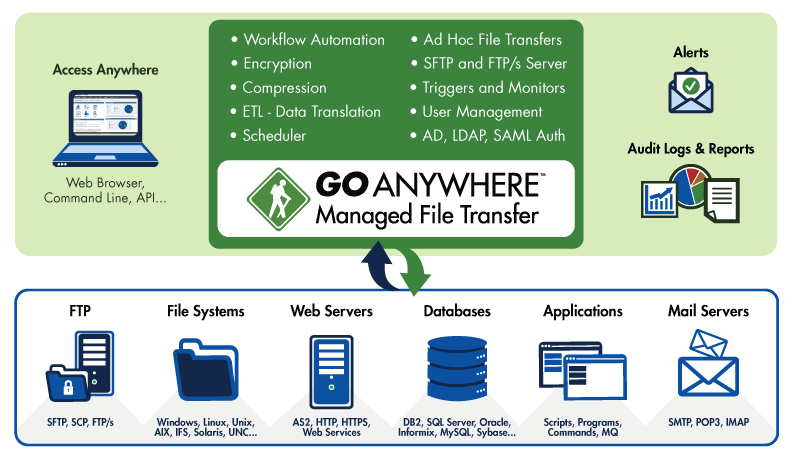
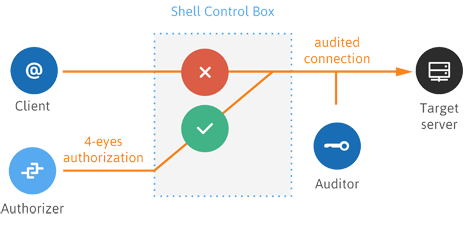
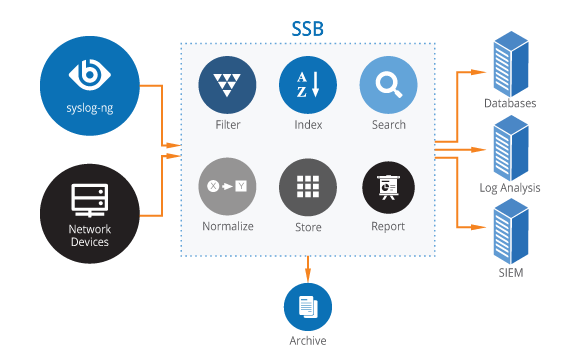
Enterprise SFTP and key management Tectia SSH Client and Server are fully interoperable with OpenSSH and standard SSHv2-compliant third-party implementations. You have the flexibility to stay secure with partners, subcontractors and in hybrid environments. With UKM you can centrally manage large SSH key inventories – in the thousands or millions – and automate policy enforcement, consolidate visibility […]