Detect & Identify
Threat detection in the IT network is the practice of analysing the entirety of a security ecosystem to identify any malicious activity that could compromise the network.
If a threat is detected, then mitigation efforts must be
enacted to properly neutralise the threat before it can exploit any present vulnerabilities.

TianJi Partners — Digital Risk Protection (DRP) & Threat Intelligence
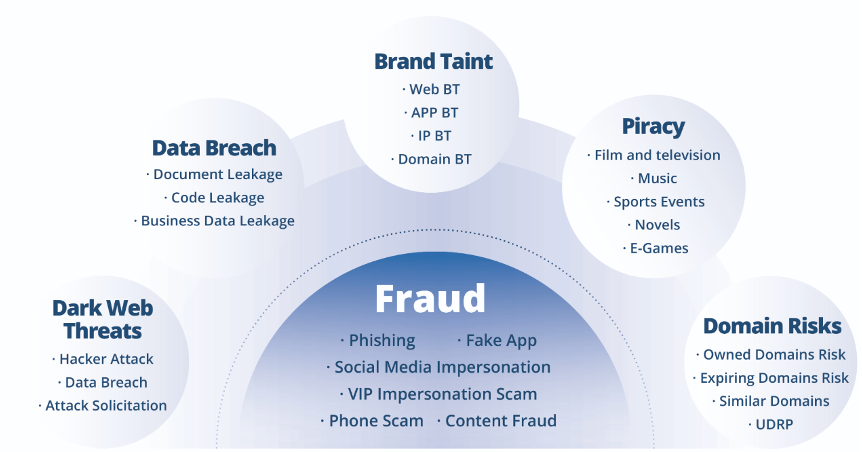
TianJi Partners provides advanced Digital Risk Protection (DRP) and global Threat Intelligence to help organisations identify, monitor, and eliminate external digital threats. The platform delivers high-accuracy detection, multilingual coverage, and industry-leading takedown capabilities, making it ideal for enterprises operating across complex international threat surfaces.
With automated monitoring, large-scale intelligence feeds, and a powerful analysis interface, TianJi Partners enables security teams to respond faster, protect brand reputation, and reduce digital risk across web, social media, mobile apps, and dark web environments.
Why Choose TianJi Partners?
- High-accuracy global monitoring across web, social media, mobile, and dark web
- Industry-leading takedown performance, especially in Chinese-language regions
- Large-scale threat intelligence feeds for investigation and enrichment
- SaaS platform with multi-language support and an intuitive UI
- Real-time alerts for phishing, brand abuse, rogue apps, and threat actor activity
- APAC-focused coverage for faster, regionally aligned response
Digital Risk Protection (DRP)
Key Highlights
- 24/7 global monitoring for phishing, fake websites, rogue apps, impersonation
- High-accuracy detection with multilingual coverage
- Fast takedown support, especially strong in Chinese-language regions
- Real-time alerts via SaaS dashboard
Core Features (Very Short)
- Monitors web, social media, app stores, dark web
- Automated detection + case tracking
- Easy-to-use platform with multi-language UI
Benefits
- Lower workload for security teams
- Protects brand safety & customer trust
- Reduces exposure time with fast takedown
Threat Intelligence Subscription (TI-Feed & TI-Lookup)
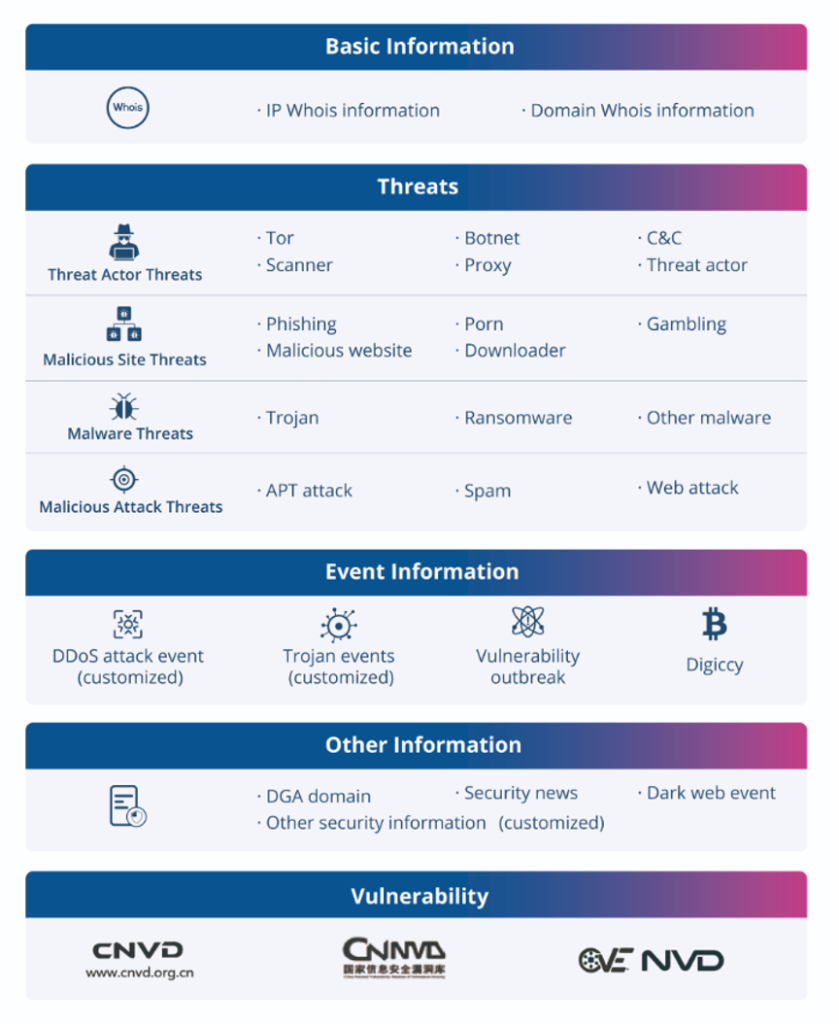
Key Highlights
- 100M+ threat indicators daily
- Plaintext feeds for easy SOC/SIEM integration
- On-demand threat lookup with context and reputation scoring
Core Features (Very Short)
- Bulk feeds: malicious IPs, domains, URLs, hashes
- Lookup provides: reputation, related infrastructure, timeline
Benefits
- Better visibility of active threats
- Faster investigations & response
- Improves SIEM/SOAR accuracy

Featured products:
Digital Risk Protection (DRP)
Threat Intelligence Subscription (TI-Feed & TI-Lookup)
Advanced Log Management for Enhanced Security and Compliance
As a leader in log management, syslog-ng Premium Edition and Syslog-ng Store Box (SSB) provide powerful solutions for collecting, filtering, transforming, enriching, and delivering logs. Designed for enterprises, syslog-ng ensures seamless log management, enhanced security, and compliance with audit and cyber threat detection requirements.
Why Choose Syslog-ng Premium Edition?
- Unmatched Log Management : The most widely adopted log management software globally, syslog-ng is built for enterprises handling large-scale data loads.
- Scalable Efficiency : Route logs to multiple destinations from a single instance with unparalleled efficiency and flexibility.
- Advanced Reliability : Ensure minimal log loss with Advanced Log Transport Protocol (ALTP) , disk-buffering , and flow control mechanisms.
- Enterprise-Grade Security : Enable full log encryption both in transit and at rest, protecting sensitive data from cyber threats.
- Seamless Integration : Compatible with hybrid environments, syslog-ng supports diverse infrastructure setups for both on-premises and cloud-based systems.
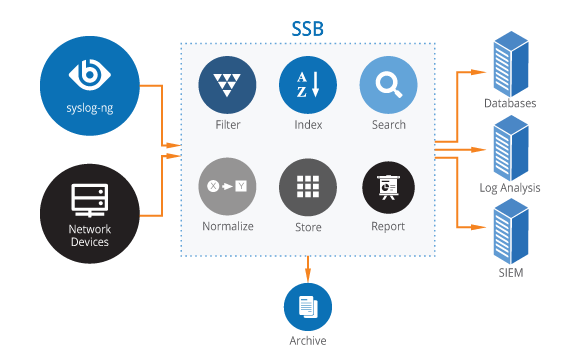
Syslog-ng Store Box (SSB) – Centralized Log Storage and Analysis
Syslog-ng Store Box complements the Premium Edition by providing a centralized log storage and monitoring solution:
- Secure Log Archiving : Efficiently store and archive logs with tamper-proof protection.
- Real-Time Monitoring : Gain visibility into log activities to detect threats and ensure continuous compliance.
- High Availability : Built with robust failover support, SSB guarantees reliable performance and minimal downtime.
- Audit-Ready Reporting : Generate compliance-ready reports for internal audits or regulatory requirements effortlessly.
- Simplified Management : Unified interface for easy access, search, and analysis of logs.
Key Benefits for Your Enterprise
- Cyber Threat Detection : Identify and mitigate threats faster with enriched and centralized log data.
- Compliance Simplified : Meet regulatory standards with robust logging, monitoring, and reporting tools.
- Cost and Resource Efficiency : Reduce errors, save time, and enhance productivity by consolidating log management and delivering actionable insights.
Contact us today to discover how syslog-ng can enhance your security operations and ensure compliance in a fast-evolving threat landscape.

Featured products:
syslog-ng Premium Edition
syslog-ng Store Box (SSB)
AXOFLOW — Security Log Classification, Curation & Data Routing
Axoflow delivers a fully intelligent security data pipeline platform that automatically classifies, curates, enriches, and routes log data across the enterprise. Designed to eliminate routine ingestion engineering, Axoflow reduces SIEM costs, improves investigation speed, and provides end-to-end visibility into the entire data flow.
Its zero-maintenance connectors, real-time observability, and policy-driven routing engine allow security teams to standardise, optimise, and control their log data at scale — across SaaS, cloud, on-premise, and air-gapped environments.
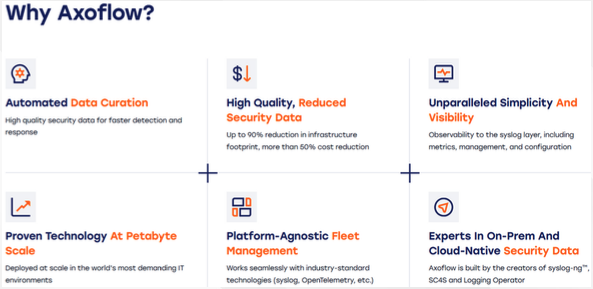
Why Choose Axoflow?
- Zero-maintenance connectors that auto-detect log sources
- Automatic classification with no parsers or regex
- Advanced data curation (filtering, parsing, enrichment, reduction)
- 50%+ SIEM cost reduction
- Up to 70% faster investigations
- Real-time pipeline metrics & full observability
- Policy-based routing for business, compliance, and cost rules
- Vendor-agnostic & scalable for enterprise SOC operations
Axoflow Collection Platform
1) Zero-Maintenance Connectors
Key Highlights:
- Automatically detect log source types
- Pre-configured logic for common security/network devices
- No manual parser creation required
- Instantly ready for ingestion pipelines
2) Automatic Classification & Source Detection
Key Highlights:
- Identifies the origin and category of each log
- Adds metadata & prepares logs for SIEM/SOAR/XDR
- Works across syslog, cloud logs, agent logs, proprietary formats
3) Data Curation & Reduction Engine
Key Highlights:
- Filters noise and redundant log lines
- Parses and enriches with contextual data
- Normalises logs for consistent schema
- Reduces raw data volume by 50%+
4) Policy-Based Routing (Smart Business Routing)
Key Highlights:
- Route logs to SIEM, data lake, archive, or storage tier
- Business-driven routing (cost, compliance, retention)
- No regex or scripting — visual rule builder
- Supports multi-destination fan-out delivery
5) Full Observability & Real-Time Metrics
Key Highlights:
- Dashboards for pipeline health, throughput, anomalies
- Monitor log volume spikes, ingestion failures, delays
- Full visibility even in on-prem or air-gapped deployments
6) Flexible Deployment Options
Key Highlights:
- SaaS hosted
- Self-managed on Kubernetes
- Private cloud / hybrid
- Fully air-gapped deployment for high-security environments


Featured products:
Axoflow Collection Platform
Detect & Identify